Midnight Flag CTF 2k25 - Samurai write-up
Last weekend I was looking for a reverse Windows challenge. The Midnight Flag CTF provides one challenge of this kind (difficulty : easy). Here is a short write-up & lessons learned about it.
About Midnight Flag CTF
In the field of computer security, the CTF (Capture the Flag) is a type of competitive event or challenge designed to test participants’ skills in various aspect, to find and/or exploit vulnerabilities affecting software, websites or computer systems in order to get a flag (drapeau in French).
The Midnight Flag CTF is the annual cybersecurity competition organized by ESNA students
Samurai write-up
Here is the challenge :
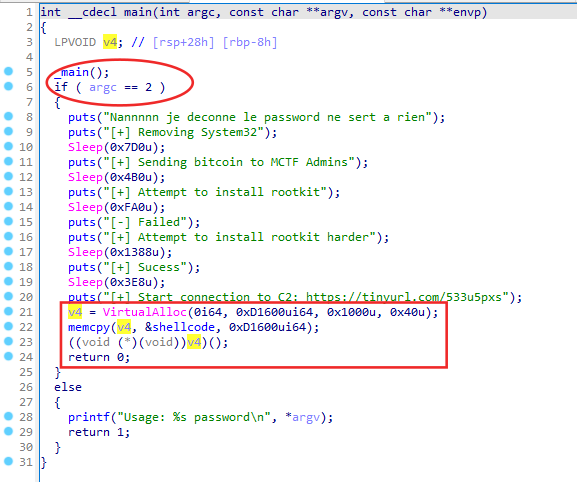
The main() of oscur.exe is very simple :
-
we must start the executable with an argument
-
after some troll operations using puts + Sleep, the program allocate 0xD1600 which it fill with the shellcode then execute it
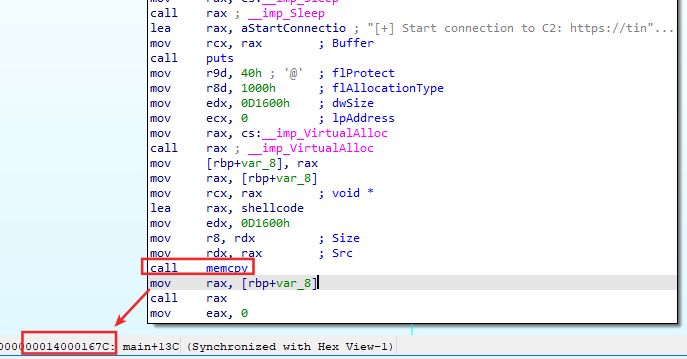
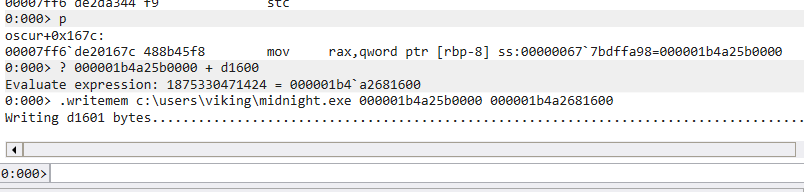
We will extract the shellcode by breaking just after memcpy then dump the heap.
Let’s doing it in Windbg.
We set the breakpoint at oscur+0x167c, then dump the shellcode to a new file we named midnight.exe (indeed we know it’s an exe file thanks to magic bytes at the beginning of the shellcode).
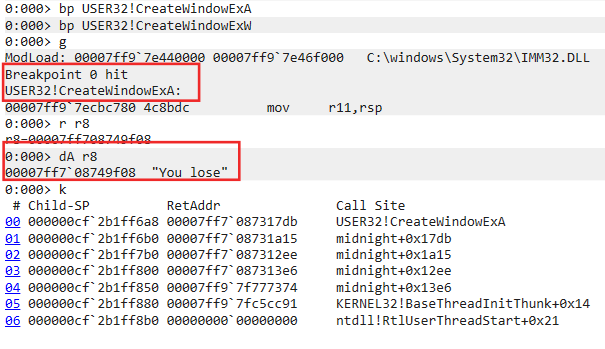
When running midnight.exe for the first time in windbg, this window “You lose” is displayed.
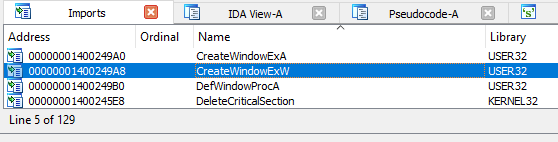
We look at the (129 !!) imports in order to find the Windows API used for creating this window : CreateWindowEx
Set a breakpoint onto CreateWindowEx, then check the call stack when the window pop up :
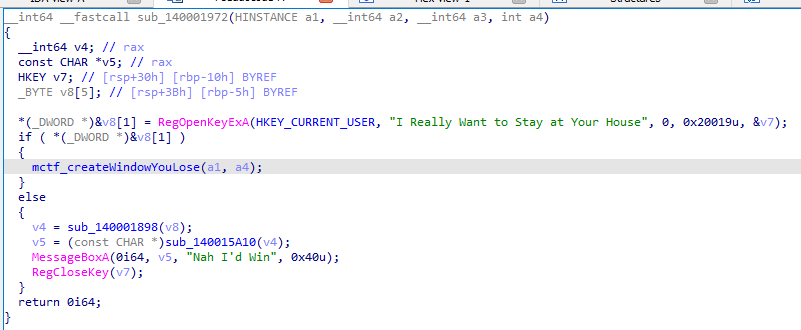
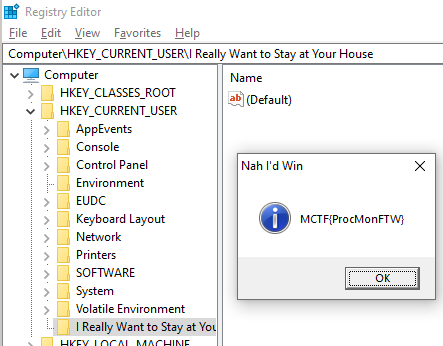
Then we look at the previous call from the call stack, at midnight+0x1a15. This function tests the registry key HKCU\I Really Want to Stay at Your House.
If the key doesn’t exist, then goto FAIL, else goto WIN (MessageBox).
Ok let’s create the registry key and test : the flag is displayed directly MCTF{ProcMonFTW}
Lessons learned
A CTF is an opportunity to learn new techniques, and here are the lessons I drew from it :
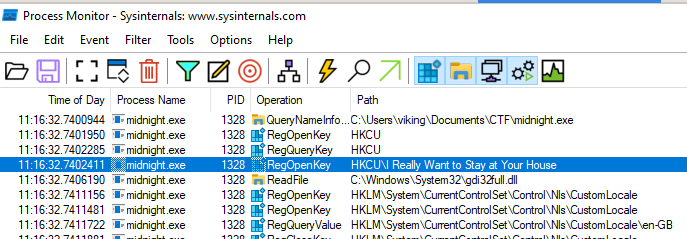
- the Procmon tool should not be forgotten during reverse operations. The author of the chall probably solve it with Procmon (the flag says ProcMonFTW). Of course we can see the registry key that should be read (HKCU\I Really Want to Stay at Your House) but this idea did not come to my mind
- The
.writememcommand of Windbg writes a section of memory to a file. It is useful when you want to extract a payload / stage 2 / shellcode of RAM.
Thanks for reading, I hope you learnt something and your feedbacks are welcome !
Resources :
https://midnightflag.fr/
https://learn.microsoft.com/en-us/sysinternals/downloads/procmon
https://learn.microsoft.com/en-us/windows-hardware/drivers/debuggercmds/-writemem–write-memory-to-file-